UAV with DTOE-AOF implementation
Bettering effectivity, lowering latency, and profiting from accessible sources have gotten more and more vital within the ever-changing world of UAV operations. Latency, bandwidth limitations, and scalability issues are issues with conventional central processing strategies. This research presents the DTOE-AOF to deal with these points. With AI-powered selections and edge computing buildings, DTOE-AOF could dynamically assign computing jobs to UAVs and edge nodes in response to proximity, accessible sources, and the urgency of the work. With its groundbreaking methodology, DTOE-AOF is poised to revolutionize numerous packages, from agricultural precision to emergency administration, by decreasing latency, growing mission effectivity, and conserving sources.
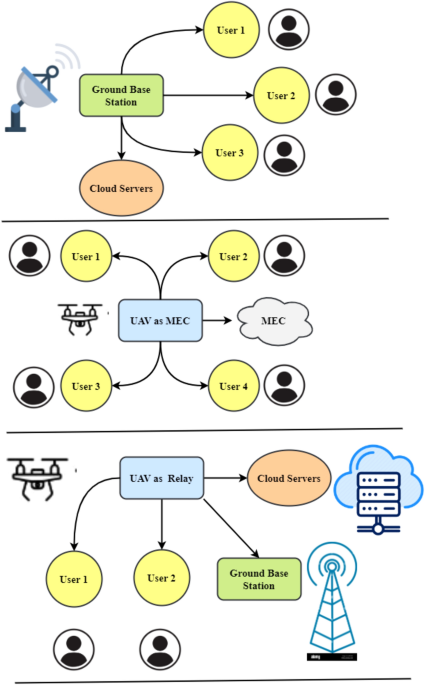
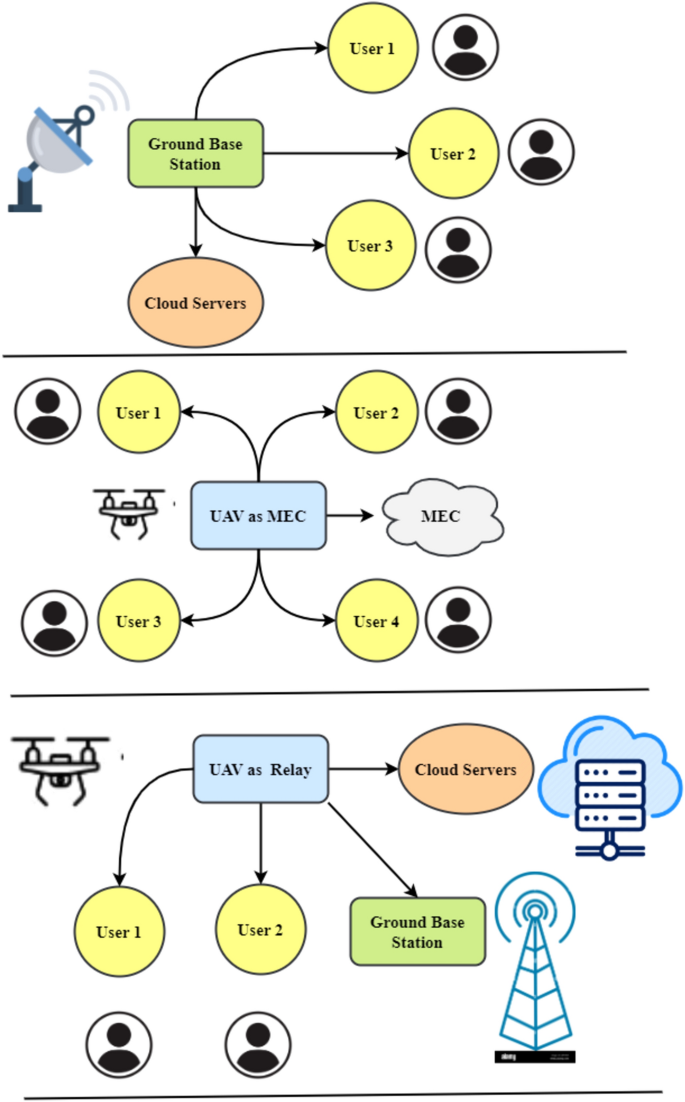
MEC is often acknowledged as a fundamental expertise for numerous next-generation IoT functions. Resulting from their versatility and ease of deployment, UAVs can present edge computing companies. UAV-enabled MEC designs could also be categorized and utilized. A UAV could also be a relay, IoT node, or cell EC server. First, UAVs could act as cell nodes by sending their computing energy to a MEC server. Because the MEC, the UAV could monitor a cluster. The third utilization of UAVs is linking cell finish nodes to MEC servers. Determine 1 reveals that the UAV could submit memory- and processing-intensive operations to an MEC server as a devoted consumer. Advanced computational jobs could also be too tough for UAVs’ processing, reminiscence, and battery life. Transferring knowledge processing to the ground-based MEC server could prolong its battery life. Determine 1 depicts an alternate state of affairs wherein the UAV flies with the MEC server to help floor customers with computing as soon as they offload their jobs to it. Within the third different, Fig. 1, the UAV acts as a central relay to let cell customers transmit their computing operations to an MEC server.
UAV-enabled MECs’ design supplies IoT units with dependable, low-latency companies. Nonetheless, turmoil abounds. Airborne knowledge safety, storage, administration, and UAV networking are complicated. UAV mobility complicates communication, requiring larger ground-based user-UAV cooperation. The low battery energy of UAVs is one other problem. Extra energy is required for onboard computations earlier than hovering, accelerating/decelerating, climbing/descending. To start out planning for higher power and useful resource administration instantly. One other problem when growing UAV-enabled MEC methods for computing work is built-in route engineering. Predicting and monitoring cell consumer behaviour is crucial for the optimum offloading of computing duties and well timed communication of computing outcomes to customers. Many UAV MEC companies require larger trajectory design consideration. UAV blockchain integration is tough16. UAVs pose privateness points, air site visitors legislation violations, quantum assaults, machine studying, and algorithmic assaults alone.
$$L= frac{beta .left(alpha . TT+ delta . PT+ vartheta . PTright)}{sigma + rho +N pi }$$
(1)
Equation (1) makes the examination of latency (L) throughout UAV operations extra difficult. A delicate change within the significance of particular parts throughout the latency equation is made doable by the weighting (textual content{} beta), (alpha . TT), (delta . PT), and (vartheta . PT). The parameter (sigma) captures the fluctuating character of the community’s capability by modulating the affect of Wavelength on the general delay, including additional complexity. Moreover, the difficult community (N) atmosphere is mirrored within the intricate affect of the regulators (rho) and (pi) on Standing in line Time and Connection Overhead, respectively. This all-encompassing equation adequately captures the intricate interaction of things, which supplies a radical comprehension of delays in UAV operations.
$$T= frac{theta . left(mu . DS+delta . OU+tau .ETright)}{XE. sigma }+BG. omega +TS. varphi$$
(2)
Equation (2) supplies a posh components that explores the primary components that contribute to the scalability of a system, capturing the complexities of scalability the place (T) in UAV operations. Varied weights (theta), (mu), (delta), and (delta) permit for delicate modifications to the relevance of Computational Assets (DS), Community Throughput (OU), and Knowledge Storage (ET). The parameter (omega) enhances the general scalability by adjusting the affect of Workload Distribution (BG). As well as, the Adaptability Issue (XE) and System Redundancy (TS) dynamics are elaborately captured by the modifiers (omega) and (varphi). This easy components offers a full image of the complicated interrelationships that decide the scalability of UAV operations, shedding mild on the dynamics of redundancy and adaptability within the system17.
$$P= frac{beta . N{F}^{gamma }+alpha .S{U}^{theta }}{delta .S{T}^{rho }}+{sum }_{j=1}^{o}{tau }_{j}. left({mu }_{j}.{BJ}_{j}^{{L}_{j}}.{CE}_{j}^{{sigma }_{j}}.{TO}_{j}^{{tau }_{j}}proper)$$
(3)
Equation (3) incorporates a sophisticated mannequin for evaluating the efficiency (P) of UAV operations. The significance of mission effectivity the place (N{F}^{gamma }), response time (S{U}^{theta }), and useful resource utilisation (S{T}^{rho }) are represented by the weighted coefficients (beta), (alpha ,) and (delta), respectively. Equational intricacy is enhanced by the inclusion of non-linear exponents similar to ({TO}_{j}^{{tau }_{j}}), (mu), and ({sigma }_{j}), which magnifies the affect of those fundamental components on total efficiency by capturing complicated dependencies. Moreover, by making an allowance for additional components like AI integration, edge computing (CE) capabilities, and dynamic job offloading strategies, the phrases concerned add a larger diploma of complexity.
UAV with MEC implementation
MEC solves the cell IoT gadget useful resource and time subject. Backhaul congestion and community latency could also be lowered with extra CC merchandise. UAVs with knowledge storage, processing, and communication could deploy MEC servers at community edges18. On this design, low-powered IoT units could outsource computation to UAVs with MEC servers through line-of-sight communication. The system should forecast duties, deploy UAVs, manage customers, analyze indicators, and allocate cooperative sources, amongst different challenges. The EC structure means that transportable and adaptable UAVs will present decentralized options. The flying edge structure’s elevated CC capabilities are ideally suited for real-time, latency-sensitive IoT functions. Transferring computation from knowledge centres to IoT units improves real-time administration and decision-making with decrease latency. An IoT system’s many endpoints flood peripheral units with knowledge.
Knowledge group and processing are wanted for automated upkeep, self-monitoring, and prediction. Because of the reminiscence and processing energy hole between EC endpoints and centralized cloud servers, sure AI methods can’t analyze edge knowledge. Any resilience-focused AI method should put together for reminiscence and processing capability restrictions. Decentralized useful resource distribution permits EC to fulfil consumer requests faster than a CC, even with minimal processing19. Work scheduling, useful resource allocation, and offloading points could dramatically affect efficiency. Over a number of a long time, AI has been extra well-liked for networking difficulties. ML is utilized in numerous areas, together with networking, for its decision-making and interplay talents. It could improve community efficiency in quite a few areas, together with useful resource allocation, site visitors classification and prediction, congestion management, and routing.
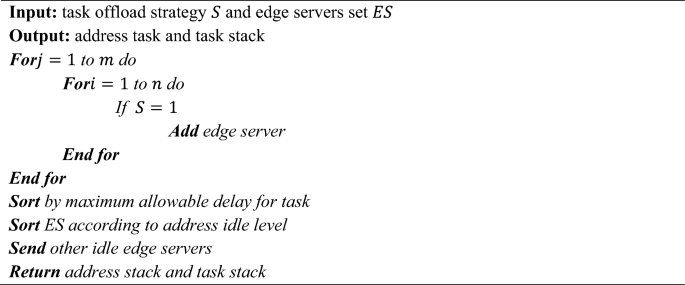
Algorithm 1 reveals the Useful resource Allocation based mostly on the proposed DTOE-AOF. Creating a useful resource allocation technique goals to extend the probability of the task’s success. Discovering the easiest way to cut back latency in cloud and edge-cloud collaboration methods requires a mixture of communication applied sciences and laptop useful resource allocation. This analysis developed a distributed computing-based offloading technique that may adapt to altering consumer masses and obtain excellent computing offloading capabilities. In an atmosphere with many channels of wi-fi interference, our analysis discovered the most effective resolution to the difficulty of offloading sources from the edge cloud to a number of customers. Allotting sources amongst edge servers is modelled on this analysis. Time is of the essence for crowd actions as properly since edge servers have restricted processing energy and cargo capability and should end computing jobs inside a sure timeframe. Consequently, this text classifies the duties by precedence and saves them within the task stack, equal to the tackle stack within the edge server, based mostly on the utmost permissible delay of the duties20.
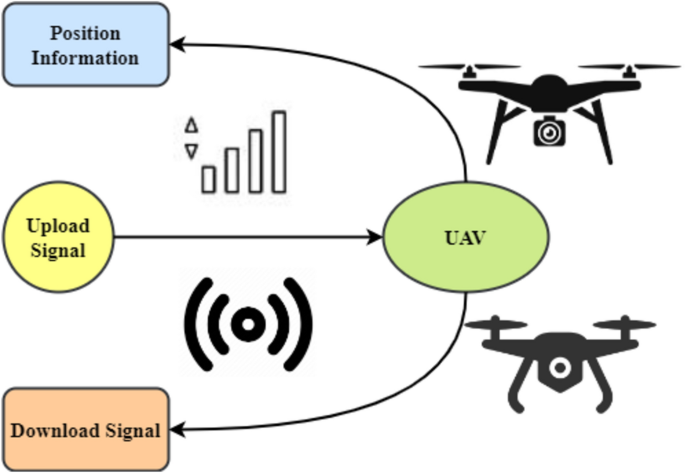
MEC methods use FMC controllers for UAVs. They sometimes seize consumer, UAV, and MEC server knowledge. This command centre oversees AI offloading. A UAV-assisted association makes use of a cloudlet like Fig. 2. After an IoT gadget completes an offloaded job, the UAV stories again. If the info requires extra complicated processing than the cloudlet can deal with, the UAV could switch it to the closest floor servers. For IoT units like smartphones, sensors, cars, and robotics, the system could use a fleet of UAVs to cowl an unlimited space. Onboard cloudlets make use of AI to deal with user-generated knowledge31.
$$DS= frac{beta {I}^{theta }.{C}^{gamma }}{alpha . A{v}^{mu }. {sum }_{j=1}^{o}{delta }_{j}. left({Au}_{j}^{{L}_{j}}. {Au}_{j}^{{pi }_{j}}.{En}_{j}^{{tau }_{j}}proper)}$$
(4)
Equation (4) incorporates a number of crucial components into an in depth mannequin, providing a radical depiction of knowledge safety (DS). This equation emphasizes the worth of defending knowledge from unauthorized entry the place (beta {I}^{theta }) because the weighted coefficient representing the significance of Confidentiality, a extra nuanced portrayal of the difficult dependencies throughout the secrecy part is made doable by including a layer of complexity by introducing the non-linear exponent (theta). Moreover, the weighted coefficient ({C}^{gamma }) highlights the importance of Availability, fixing the issue of knowledge accessibility (alpha . A{v}^{mu }) when wanted. Realizing that knowledge safety extends past easy confidentiality ({delta }_{j}), the non-linear exponent (alpha) provides complexity by providing an in depth description of the hyperlink with availability. The importance of sustaining unmodified and reliable knowledge is proven within the non-linear sensitivity of Integrity, which is captured by the exponent (delta). With their weighted coefficients and non-linear sensitivities, the phrases (pi), (tau), and j add complexity to the equation, which allows the inclusion of extra components like encryption ({En}_{j}^{{tau }_{j}}), authentication ({Au}_{j}^{{L}_{j}}), and authorization ({Au}_{j}^{{pi }_{j}}).
$$Pr= frac{Delta .{TP}^{nabla }}{alpha . {TP}^{theta }+beta . {FP}^{delta }+{sum }_{j=1}^{o}{rho }_{j}. left(PPV. Sright)}$$
(5)
Precision (Pr) is a vital measure in classification duties, and Eq. (5) reveals a posh mannequin for it. The significance of True Positives the place ({TP}^{theta }), that are positively (PPV) acknowledged, and False Positives ({FP}^{delta }), that are negatively linked with incorrectly labelled constructive cases, are proven by the weighted coefficients, which can be represented by symbols like (Delta), (nabla), and (alpha). The complicated interdependencies (S) inside these elements are captured by including non-linear exponents (beta), (rho), and (theta), which introduce a delicate sensitivity to modifications.
$$MEff= frac{beta .{OT}^{gamma }}{alpha .{IT}^{theta }+delta . {DT}^{varepsilon }+{sum }_{j=1}^{o}left(Ut. ECright)}$$
(6)
Equation (6) introduces a complete mannequin for assessing machine effectivity (MEff), contemplating numerous crucial components within the manufacturing course of. The weighted coefficients the place (beta), (alpha), and (delta), characterize the importance of Output ({OT}^{gamma }), Enter (alpha .{IT}^{theta }), and Downtime (delta . {DT}^{varepsilon }), respectively, in figuring out the general effectivity of a machine21. Together with non-linear exponents, (varepsilon), j, and o provides intricacy by capturing complicated dependencies inside every part, permitting for a extra nuanced understanding of their affect on effectivity on utilization (Ut) and power consumption (EC).
DTOE-AOF and DTOE-AIF implementation
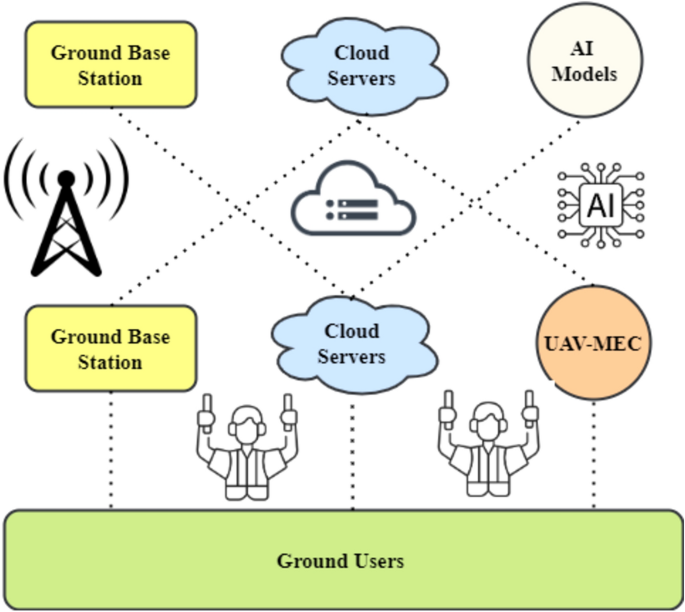
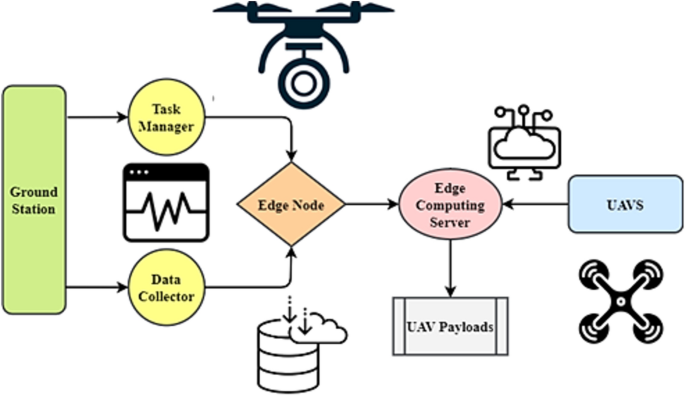
The framework in Fig. 3 reveals a complete dynamic task offloading and edge-aware optimization mechanism for clever and environment friendly UAV operations. The structure’s interconnected items present simple communication, sensible decision-making, and useful resource effectivity22,23. The bottom station is the system’s hub for managing obligations and gathering knowledge. Knowledge Collector and Task Supervisor are essential Floor Station parts. The Knowledge Collector gathers knowledge from quite a few sources for evaluation and decision-making, whereas the Task Supervisor orchestrates duties to maximise execution. Wi-Fi and 5G inner communication channels permit the Floor Station and Edge Node to speak properly. Edge computing permits the Edge Node to arbitrate Floor Station-UAV communication, boosting processing effectivity and latency.
The Edge Computing Server on the Edge Node controls operations with its AI Inference Engine and Task Scheduler. These items allow clever work allocation and real-time knowledge processing, bettering system efficiency. The server-UAV connection utilizing LoRa and RF ensures dependable and low-latency knowledge supply. UAVs have Edge Gadgets, that are small computer systems for onboard processing. These edge units join UAV payloads with thermal sensors, LiDAR, and cameras. On this design, UAVs could collect and consider sensory knowledge in real-time to make knowledgeable judgments.Dynamic offloading lets the framework adapt to altering workloads and circumstances. By contemplating compute load, latency necessities, and power effectivity, edge-ware optimization ensures an affordable task allocation between the Edge Computing Server and onboard Edge Gadgets. Flexibility boosts UAV responsiveness and effectivity.
$$RT= frac{rho . {TTC}^{mu }}{WT.tau +PT.sigma +{sum }_{j=1}^{o}{beta }_{j}}$$
(7)
Equation (7) presents a sophisticated mannequin for measuring responsetime (RT). Contemplating the processing time (textual content{the place } sigma), ready time (WT.tau), and job completion time (PT.sigma) extra facets like concurrency, useful resource availability, and community latency. With this equation, it optimizes the responsiveness ({TTC}^{mu }) of a system in each doable state of affairs by contemplating the complicated nature of response time in several settings.
$$RU= frac{omega .AU}{{IT}^{epsilon }.beta + {MCy}^{sigma }.epsilon +{sum }_{j=1}^{o}{varphi }_{j}}$$
(8)
Equation (8) is an entire and complicated mannequin for the nuanced analysis of useful resource utilization (RU). The weighted coefficient (omega), which emphasizes the worth of Precise Utilisation (AU). The equation can seize complicated relationships in the actual utilization part since non-linearity is launched by together with the exponent ({IT}^{epsilon }). The impact of Most Capability (MC) is highlighted by (beta), and the non-linear sensitivity is launched by the accompanying exponent (sigma), which acknowledges the complicated hyperlink between useful resource effectivity and fluctuations in most capability. The delicate affect of idle time on the general effectivity of useful resource utilization is captured by the exponent j whereas (varphi) determines the affect of Idle Time, which represents durations when a useful resource will not be in use.
$$S= frac{{TP}^{alpha } . beta }{left(FN+TPright). alpha +{sum }_{ok=1}^{p}{FSe}_{ok}^{{ok}_{j}}}$$
(9)
A posh and detailed mannequin for sensitivity (S) analysis is proven in Eq. (9), which considers a number of facets that have an effect on the accuracy of a mannequin for classification in detecting constructive instances. The weighting issue the place (alpha) highlights the relevance of True Positives (TP), making it clear how vital it’s to accurately detect constructive instances and add to the overall sensitivity (FS). Incorporating non-linearity, the coefficient (beta) captures complicated relationships inside the actual constructive part, enabling a extra detailed portrayal of its affect. Past True Optimistic checks, (p) highlights the mixed affect of real positives and FalseNegatives (FN), acknowledging the interconnectedness of positively detected instances and negatively classed conditions. A further layer of complexity is launched by the exponent ok, which displays the mixed impact of variations in true positives and false negatives on sensitivity j, leading to non-linear sensitivity to those variables.
UAV-aided wi-fi community implementation
The proposed UAV-aided wi-fi community concept addresses the challenges of working in areas with out indicators and poor communication infrastructure. This method makes use of an Endpoint Gadget (ED) to gather, analyze, and switch knowledge to the cloud in real-time. The proposal recommends using UAVs as cell base stations to offer non permanent communication hyperlinks in areas with out bodily connections18. Determine 4 reveals the UAV-aided web structure in 3D with two-hop full-duplex communication. With this payload, the UAV could briefly connect with a signal-less atmosphere. The UAV could relay after connecting to an entry level in a signal-bearing zone.
The relay system makes use of amplify-and-forward (AF). This methodology amplifies the incoming sign with out demodulating or modulating. Sign processing is simplified by this expertise, making it acceptable for UAV operations in distant locations with restricted computing sources. The beneficial resolution will increase communication vary by deploying UAV-assisted relays to bypass sign restrictions in difficult conditions. A two-hop full-duplex switch state of affairs ensures full knowledge supply between the ED and the cloud. Utilizing the bridge the UAV momentarily places up, the ED can switch knowledge to the cloud even with out a sign. The mannequin considers UAV-assisted relay constructing time- and space-related dynamics in three dimensions for correct placement and motion. The beneficial communication methodology makes use of the amplify-and-forward technique, which is mathematically acknowledged to elucidate sign reception and transmission. This research proposes a wi-fi community that may work together in poor sign areas utilizing UAVs with amplify-and-forward relay strategies. This distinctive approach could also be used for catastrophe reduction, distant sensing, and different areas missing communication networks.
$$R= frac{{PoS}^{partial }. beta }{{{{A }^{tau }V}^{delta }}^{mu }. alpha +(R . Re)}$$
(10)
For an in depth analysis of a system’s robustness (R), Eq. (10) supplies an entire and complicated mannequin. The significance of System Efficiency is proven by the weighted coefficient,the place ({PoS}^{partial }), which highlights the overall system performance’s holistic worth in figuring out the system’s robustness. By together with the exponent ({{{A }^{tau }V}^{delta }}^{mu }), non-linearity is launched, permitting the system efficiency part to seize complicated relationships (delta). As a result of the system will not be linear, the consequences of efficiency fluctuations ((R . Re)) on the system’s resilience (alpha) could also be extra exactly and nuancedly depicted.
$${I}_{j}={i}_{o}{exists }_{j}^{-2}frac{{i}_{o}}{{I}^{2}+Vert {q}_{N}-{q}_{V}Vert }, Jin M$$
(11)
Within the Eq. (11), the place the gap between ({I}_{j}) and the MES is denoted as ({i}_{o}), and the channel achieve at a reference distance the place ({i}_{o}), ({I}^{2}), could also be used to calculate the channel achieve between ({q}_{N}) and the ({q}_{V}).
$${S}_{j}= frac{C}{o}{log}_{2}left(1+frac{{Q}_{u}{left|{I}_{j}proper|}^{2}}{{Y}^{2}}proper), Jin M$$
(12)
Within the Eq. (12), the place ({S}_{j}) is the transmission bandwidth between the C and the O; for offloading communication ({Q}_{u}), it may be additional break up into ({I}_{j}) and ({Y}^{2}) sub-bands.
Vitality optimization course of
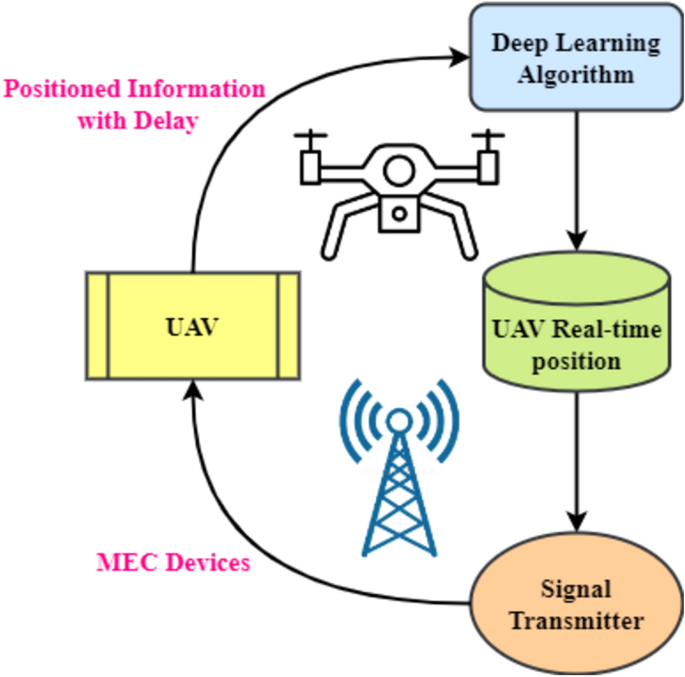
Inefficiency attributable to mounted emission power for knowledge transmission should be thought of to elongate Edge Gadgets (EDs) working time by avoiding power loss. Predetermined emission power could lead to obtained sign power that exceeds receiver sensitivity, losing power and decreasing effectivity. To deal with this problem, a singular DL-based power optimization approach adapts emission power ranges to ambient components. This algorithm’s implementation framework is proven in Fig. 524. The instructed methodology dynamically adjusts emission power ranges to extend power effectivity and ED operational time. This system begins with subject formulation to find and quantify environmental components affecting emission power underneath constrained circumstances.
Subsequent, a DL approach creates a prediction mannequin to handle transmission time delay-induced environmental variable uncertainties. DL’s capability to acknowledge complicated knowledge patterns helps forecast the suitable emission power ranges relying on environmental parameters. Determine 5 reveals the algorithm’s knowledge gathering, mannequin improvement, and power optimization phases. Sensors seize environmental knowledge and add it to the prediction mannequin to calculate emissions power. The DL algorithm learns from previous knowledge and adapts to new situations to anticipate ideally suited emission power ranges in real-time. This reduces transmission delays.
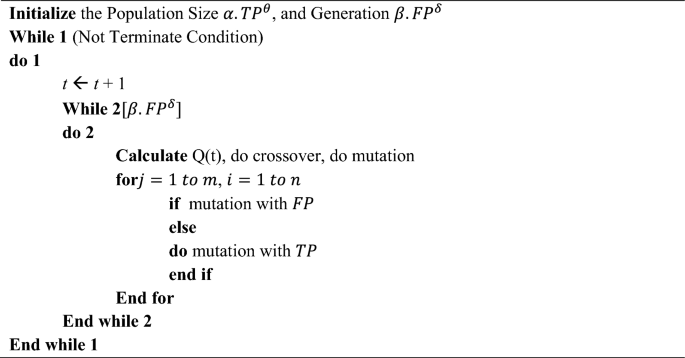
Algorithm 2 reveals the UAVs for Energy Load Matching of ML System-based task offloading technique. Random initialization of the actor-network and critic-network parameters is carried out to start with stage of coaching. Following coaching, this analysis normalizes the state observations, feeds them into the hybrid motion community, and produces steady and discrete motion distributions. Subsequent, the coverage is executed, and the UAV is rewarded. On this occasion, the processing is weak to abortion if the UAV travels outdoors of the designated area. Our research has real-world functions when pure catastrophes injury communication tools or when there’s a have to briefly unload knowledge volumes in hotspots, the place it’s doable to deploy adaptable UAVs rapidly. Learning flight planning and task-offloading procedures is crucial and reveals promise.The adaptive DL-based power optimization system can dynamically adapt to altering environmental circumstances by modifying its predictions as recent knowledge is collected. The approach optimizes emission power ranges utilizing real-time knowledge to cut back power waste and improve ED working period in resource-constrained contexts. DL-based power optimization solves the mounted emission power constraint sooner or later, bettering ED power effectivity. Actual-time prediction and adaptation optimize power utilization, extending operational instances and bettering efficiency in energy-saving settings.
$${rho }_{j}=Qsleft{{ni }_{M}ge {ni }_{U}^{j}proper}={int }_{{omega }_{th}^{j}}^{varphi }{f}^{-y}dy={f}^{-{mu }_{U}^{j}}$$
(13)
Throughout the framework of a reliability research, the likelihood density perform (PDF) of a random variable ({rho }_{j}) is described by Eq. (13)25. Within the interval the place the upkeep of the depth ({ni }_{M}) is the same as (Qs) or bigger than the use depth ({ni }_{U}^{j}), the integral of the PDF (f) over Qs is used to find out the variable ({omega }_{th}^{j}). The combination is carried out as (varphi) from the brink worth ({f}^{-y}dy).
$${ni }_{m}^{j}=frac{{d}_{j}}{{g}_{m}^{j}}+{Delta }_{j}left(left(1-nabla proper){partial }_{M}+delta proper)$$
(14)
It looks as if Eq. (14) describes a connection utilizing variables the place ({ni }_{m}^{j}) and a few constants. A extra thorough clarification of the symbols, terminology,and additional context would drastically help in offering a extra correct interpretation. Nonetheless, in response to well-liked mathematical modelling notations, it seems to face for a components that expresses the upkeep depth ({d}_{j}) as a perform of ({g}_{m}^{j}), ({Delta }_{j}), (1-nabla , {partial }_{M}), and (delta .) Some methods or processes could have a relationship between the speed or depth of upkeep.
$${P}_{m}^{j}= in {U}_{m}^{j}+left(1-ni proper){vartheta }_{m}^{j}$$
(15)
the place the amount ({P}_{m}^{j}) is proven mathematically as a mix of two phrases the place (in {U}_{m}^{j}+left(1-ni proper)). Potential variables or features on this equation embrace ({U}_{m}^{j}) and ({vartheta }_{m}^{j}), with (ni) performing as a relentless or coefficient.
The DTOE-AOF and DTOE-AIF framework are are developed to enhance the allocation of computing duties between central cloud servers and edge units. It’s a dynamic analysis of things similar to computational load, power consumption, and community latency that this framework makes use of to search out the perfect execution website for every operation. The system makes use of real-time knowledge and predictive algorithms to make sure that fast consideration computations are carried out on edge units. It additionally ensures that computations that require extra sources are transmitted to the cloud. The potential of this edge-aware methodology to extend total system efficiency, reduce latency, and protect bandwidth is of nice benefit to functions which can be built-in into the IoT, sensible cities, and autonomous methods. The framework can successfully deal with distant computing sources in ever-changing circumstances and workloads due to its flexibility and flexibility.
The DTOE-AOF and DTOE-AIF stands out as a trailblazing resolution that efficiently tackles the issues that include UAV operations. Optimizing task allocation in response to proximity and strain, DTOE-AOF achieves large mission effectivity, response time, and useful resource utilization advantages by seamlessly combining AI algorithms with computing edge capabilities. Its versatility, confirmed by many modelling research, highlights its risk of remodeling UAV operations in a number of fields. The DTOE-AOF and DTOE-AIF structure efficiency and scalability are relevant in numerous fields, from precision gardening to disaster administration. This research paves the way in which for future developments in autonomous aerial methods and improves UAV capabilities.