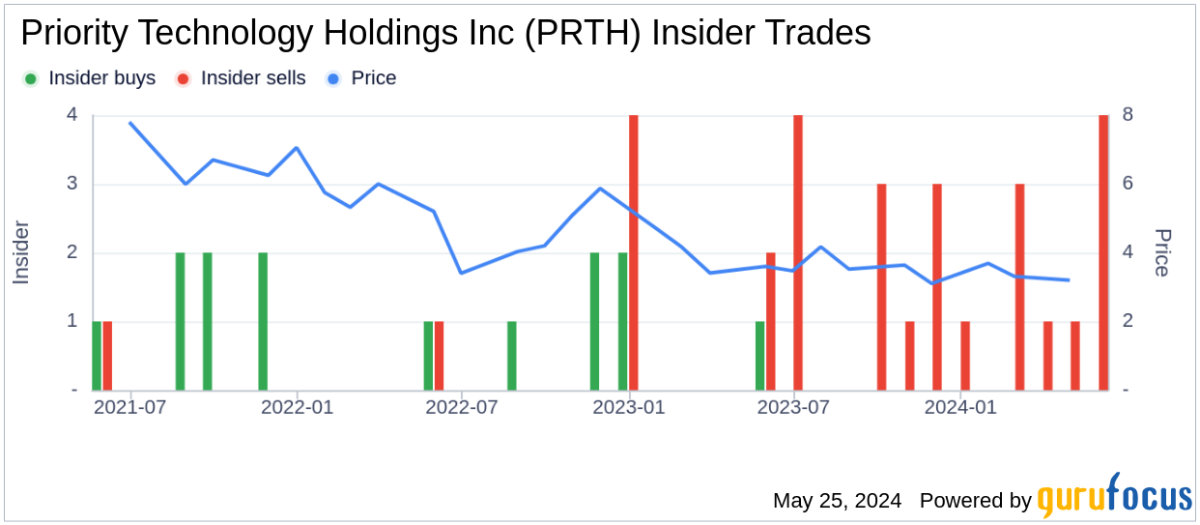
Sean Kiewiet, the Chief Strategy Officer of Priority Technology Holdings Inc (NASDAQ:PRTH), sold 59,727 shares of the company on May 24, 2024. The transaction was filed on the same day with the SEC. Following this sale, the insider now owns 1,241,853 shares of Priority Technology Holdings Inc.
Priority Technology Holdings Inc operates as a provider of merchant acquiring and commercial payment solutions. The company offers a platform for merchants, banks, and distribution partners to grow their businesses through payment processing.
Over the past year, Sean Kiewiet has sold a total of 263,951 shares and has not made any purchases of the company’s stock. The insider transaction history for Priority Technology Holdings Inc shows a trend with 1 insider buy and 22 insider sells over the past year.
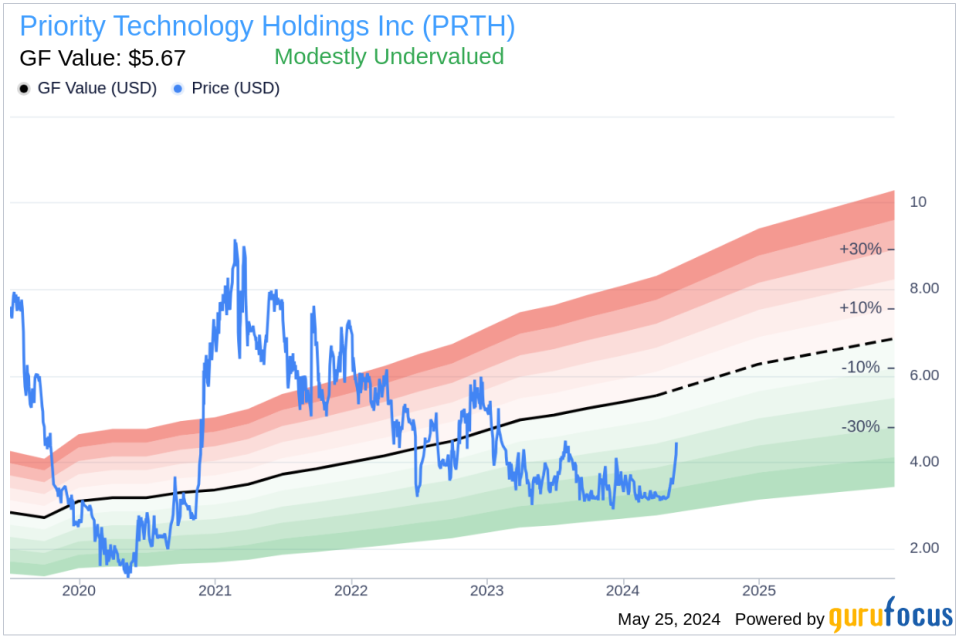
On the day of the latest transaction, shares of Priority Technology Holdings Inc were trading at $3.83, giving the company a market cap of $357.091 million. According to the GF Value, the stock is considered modestly undervalued with a price-to-GF-Value ratio of 0.68, based on a GF Value of $5.67.
The GF Value is calculated considering historical multiples such as price-earnings ratio, price-sales ratio, price-book ratio, and price-to-free cash flow. It also includes adjustments based on past returns and growth, and future business performance estimates from analysts.


This article, generated by GuruFocus, is designed to provide general insights and is not tailored financial advice. Our commentary is rooted in historical data and analyst projections, utilizing an impartial methodology, and is not intended to serve as specific investment guidance. It does not formulate a recommendation to purchase or divest any stock and does not consider individual investment objectives or financial circumstances. Our objective is to deliver long-term, fundamental data-driven analysis. Be aware that our analysis might not incorporate the most recent, price-sensitive company announcements or qualitative information. GuruFocus holds no position in the stocks mentioned herein.
This article first appeared on GuruFocus.