
New research reveals that ransomware assaults on VMware ESXi infrastructure follow a consistent pattern, independent of the file-encrypting malware used.
“Virtualization platforms are a core component of organizational IT infrastructure, yet they often suffer from inherent misconfigurations and vulnerabilities, making them a lucrative and highly effective target for threat actors to abuse,” cybersecurity firm Sygnia said in a report shared with The Hacker News.
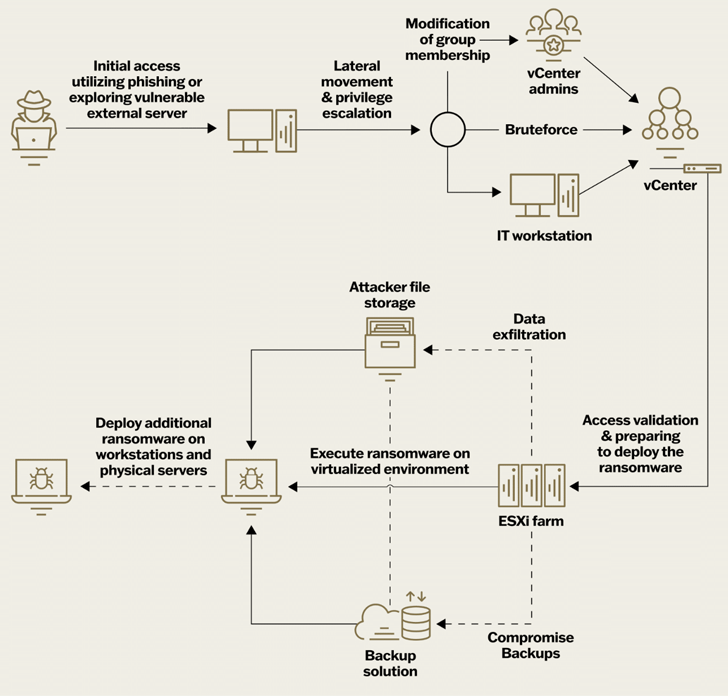
The Israeli business discovered that attacks on virtualization environments follow a similar pattern of events through its incident response work with different ransomware families, including LockBit, HelloKitty, BlackMatter, RedAlert (N13V), Scattered Spider, Akira, Cactus, BlackCat, and Cheerscrypt.
This entails taking the subsequent actions:
- Gaining first access by means of phishing scams, downloading malicious files, and taking advantage of known flaws in assets that are visible to the internet
- Escalating their privileges to use brute-force assaults or other techniques to get credentials for ESXi hosts or Center
- Establishing the ransomware and confirming their access to the virtualization infrastructure
- Destroying or encrypting backup systems, or in certain situations, altering the passwords, to make recovery attempts more difficult
- Stealing information and transferring it to other sites like Dropbox, Mega.io, or their own hosting services
- Starting the ransomware’s execution to encrypt the ESXi filesystem’s “/vmfs/volumes” subdirectory
- Spreading the ransomware to workstations and servers that aren’t virtualized in order to increase the attack’s reach
Organizations should make sure that sufficient monitoring and logging are in place, develop reliable backup plans, impose stringent authentication procedures, harden the environment, and put in place network limitations to stop lateral movement in order to reduce the dangers caused by such attacks.
The development came about after cybersecurity firm Rapid7 issued a warning on a campaign that has been going on since early March 2024 and uses malicious advertisements on popular search engines to disseminate trojanized installers for PuTTY and WinSCP via typosquatted domains, which in turn installs ransomware.
By dropping the Sliver post-exploitation toolkit through these fake installers, additional payloads are sent, such as a Cobalt Strike Beacon that is used to spread ransomware.
The action is tactically similar to other BlackCat ransomware assaults in which the initial access vector was malvertising, as part of a recurrent campaign that spreads the Nitrogen malware.
“The campaign disproportionately affects members of IT teams, who are most likely to download the trojanized files while looking for legitimate versions,” Tyler McGraw, a security researcher, stated.
“The successful execution of the malware gives the threat actor a stronger footing and impedes analysis by distorting the aim of following administrative activities.”
The discovery also comes following the introduction of new ransomware families such as Beast, MorLock, Synapse, and Trinity, with the MorLock gang specifically targeting Russian companies and encrypting files without first exfiltrating them.
“The [MorLock] attackers demand a significant ransom, which can be tens or hundreds of millions of rubles,” Group-IB’s Russian subsidiary F.A.C.C.T. claimed.
According to NCC Group data, global ransomware attacks in April 2024 decreased by 15% from the previous month, from 421 to 356.
Notably, April 2024 marks the end of LockBit’s eight-month reign as the threat actor with the most victims, showing the company’s difficulties to survive surviving a massive law enforcement takedown earlier this year.
However, in an unexpected change of events, the business reported that LockBit 3.0 had fewer than half of the detected attacks from March and was not the most prevalent threat group for the month. “Instead, Play was the most active threat group, followed shortly after by Hunters.”
Cybercriminals promoting hidden Virtual Network Computing (hVNC) and remote access services like Pandora and TMChecker that might be used for data exfiltration, distributing more malware, and enabling ransomware assaults have added to the instability in the ransomware scenario.
According to Security, a number of initial access brokers (IABs) and ransomware operators use [TMChecker] to examine hacked data that is readily available to determine whether corporate VPN and email account credentials are legitimate.
The significance of TMChecker’s concurrent growth lies in the fact that it significantly reduces the entrance hurdles for threat actors seeking high-impact corporate access for their own use or to sell to other enemies on the secondary market.

